The "Remote Control" feature of Zoom was hijacked by North Korean cryptocurrency thieves
North Korean cryptocurrency thieves have found a surprising way to use a Zoom feature for their schemes. They target cryptocurrency traders and venture investors by installing malware on their computers without being noticed.
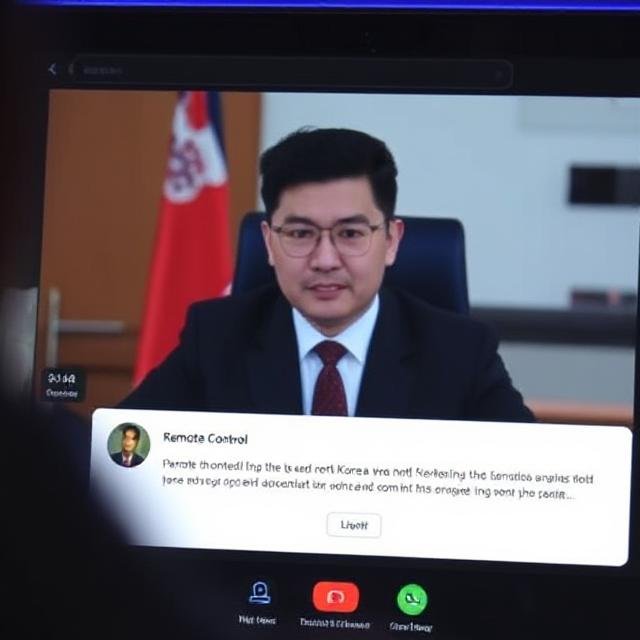
North Korean cryptocurrency thieves have found a surprising way to use a Zoom feature for their schemes. They target cryptocurrency traders and venture investors by installing malware on their computers without being noticed.
According to reports from Security Alliance (SEAL) and Trail of Bits, North Korean hackers pretend to be venture capital investors. They send fake invitations using Calendly links to lure people into attending Zoom meetings.
This operation is called Elusive Comet by SEAL. It starts with a message inviting someone to join a podcast hosted by a fake company named Aureon Capital. If the person accepts the invitation, the hackers set up a Zoom call to gather more details about their work. They might delay providing meeting details to create a sense of urgency.
During the Zoom call, hackers ask the person to share their screen. At this point, they try to trick the person into giving remote control of their computer. If the person is not careful, they might inadvertently allow this, enabling hackers to install malware on their device.
This malware can immediately steal important information or do it later. The scammers disguise their control request by changing their display name to “Zoom,” making it appear as a harmless system notification.
A single wrong click can give hackers complete control of the computer, allowing them to install various malware types. This malware can access browser sessions, password managers, and recovery phrases.
SEAL has tracked significant financial losses, amounting to "millions of dollars," due to this operation. The hackers use fake social media accounts and websites to make their activities appear legitimate.
Trail of Bits, a cybersecurity company, encountered this scam when fake profiles pretending to be Bloomberg producers attempted to schedule a meeting with their CEO.
Trail of Bits found that the criminals push last-minute Zoom meeting links that actually belong to private accounts, not business ones. They explained this trick using Zoom’s accessibility features in a few simple steps:
1. Schedule a meeting that looks genuine.
2. During the meeting, request remote control access.
3. Change the display name to “Zoom” to appear legitimate.
4. If access is given, install malware and steal data.
Zoom explicitly states that the Remote Control feature is not for unsupervised use. Still, it’s often enabled by default with no clear indicator that the request might be unsafe.
Trail of Bits believes this unclear interface is why the scam is effective. Even those knowledgeable about security may mistake it for a routine Zoom process. This risk comes from people often clicking “Approve” on Zoom requests without realizing it might give away access.
The company notes similar tactics were used in a major hack earlier this year, underlining that human error in operations is now a bigger threat than technical software flaws. This reveals that focusing tricks on people is a significant concern in the blockchain industry.














